"Apple, The FBI And iPhone Encryption: A Look At What's At Stake"
Message boards :
Politics :
"Apple, The FBI And iPhone Encryption: A Look At What's At Stake"
Message board moderation
| Author | Message |
|---|---|
|
JLDun Send message Joined: 21 Apr 06 Posts: 573 Credit: 196,101 RAC: 0 
|
|
W-K 666  Send message Joined: 18 May 99 Posts: 19048 Credit: 40,757,560 RAC: 67 
|
Doesn't give a very full set of reasons, does it. What if once the backdoor has been created, will be the US response if China, Russia or some other anti-American country demands access? |
|
JLDun Send message Joined: 21 Apr 06 Posts: 573 Credit: 196,101 RAC: 0 
|
I was watching NewsHour earlier (after the original post), where one of the "Talking Heads" brought up the point that if Apple said "Sure, we'll do this for you this one time.", that tells China/Russia/Whoever that it CAN be done, so even if Apple tells THEM no it doesn't matter if they just find someone else to try.  
|
 William Rothamel William Rothamel Send message Joined: 25 Oct 06 Posts: 3756 Credit: 1,999,735 RAC: 4 
|
I think it's like this: Software could be written (probably already exists) to allow more than ten tries at the password before the phone's data is destroyed. The FBI could then crack the password by using a sequencer that ran thru all possible password combinations. Other Apple phones would not be affected. There are 2 fears. If it is proven to work one time then Apple employees could be held for ransom until it gave the software to our enemies. If it were done just this once, then when would it end; the requests would just keep on coming. Apple can't be in the counter espionage game. Perhaps they have already done it and are practicing dis-information for the reasons I gave above. |
|
JLDun Send message Joined: 21 Apr 06 Posts: 573 Credit: 196,101 RAC: 0 
|
And the 'issue' that started the whole thing is: Some/All of the phones can be set to wipe after 10 failed attempts. The F.B.I. is not certain what this particular phone's setting is. They have a court order, telling Apple to help bypass the setting (whether or not it's there) by decrypting the phone. Of course, they are also not certain there's any information 'of value' on the phone (and it's based on "not connecting to backup for over a month", at that); but since there's a court order involved, someone did a good job convincing a judge that looking through someone else's information served the public.  
|
 Sarge Sarge Send message Joined: 25 Aug 99 Posts: 12273 Credit: 8,569,109 RAC: 79 
|
... someone did a good job convincing a judge that looking through someone else's information served the public. Am I incorrect to say the (an) issue has not been "looking at someone's information" but "looking at someone's information without reasonable cause and without a warrant"? Capitalize on this good fortune, one word can bring you round ... changes. |
 Gary Charpentier Gary Charpentier  Send message Joined: 25 Dec 00 Posts: 30640 Credit: 53,134,872 RAC: 32 
|
Am I the only one here that sees what is the end game? The FBI and all other agencies want to get data from third parties. Why? Because data that a third party has isn't subject to the protection of the fourth amendment. They can do an end run and get it with a simple subpoena and not with a court warrant. It is be time for a constitutional convention to close that loophole. 
|
|
bluestar Send message Joined: 5 Sep 12 Posts: 7019 Credit: 2,084,789 RAC: 3 |
The most likely fact is that while the CEO of Apple is strongly against putting such loopholes into their software, is the same possible to say when it comes to Microsoft? Are the updates coming from Microsoft giving both developers and other users a blank check when it comes to the possibility of access to certain information? Where are the back door or trap door being found or located here? Should we trust Norton Internet Security or AVG, or should we rather rely on a better Spy Detection Software which most likely should be able to know what you are doing as well as those things other people could be happening to do with respect to yourself? I watched the first part of the interview with the NSA chief. He is an admiral, but right now I do not recall which title I should be using here. Perhaps something like the head in charge of the NSA. If you did not know, these military men are part of the U.S. government in charge of cybersecurity and code handling. The already mentioned point is that secrets being kept in a safe is not for everyone to see. Rather the point is about the need for encrypting information in order for its contents to be sent across the web. In old days, other ways of means of doing such things were being used, including couriers for personal deliveries, but in a world having a demand for speed and efficiency, the web is the now the easiest way of doing these things. If you encrypt the sentence "the dog jumps over the lazy cat", or "the cat jumps over the lazy dog" using PGP, the contents become unreadable. But if you are using a Public Key for this purpose, most likely other people are able to know this key and is therefore able to decipher the encrypted contents. The Private Key being used to encrypt the original contents into garbled mess should be the key which should be kept secret. Both the sender and the receiver of a given message may only be having the Public Key. Neither of them knows the Private Key. The Private Key is being used to both encrypt as well as decrypt a message, making it unreadable for anyone else. How do you get Private Keys from Public Keys when using numbers? As far as I know, neither RSA-1024 or RSA-2048 have been factorized. Does perhaps the NSA know these factors already and therefore are able to listen in at your conversation? Or is perhaps information being encrypted across the web in a different way instead? |
 Lynn Lynn Send message Joined: 20 Nov 00 Posts: 14162 Credit: 79,603,650 RAC: 123 
|
Should Apple help the FBI break into a work-issued iPhone used by a gunman in the mass shooting in San Bernardino, California? I say yes. |
|
JLDun Send message Joined: 21 Apr 06 Posts: 573 Credit: 196,101 RAC: 0 
|
|
W-K 666  Send message Joined: 18 May 99 Posts: 19048 Credit: 40,757,560 RAC: 67 
|
From the BBC Apple vs the FBI - a plain English guide this is what the FBI are asking for, 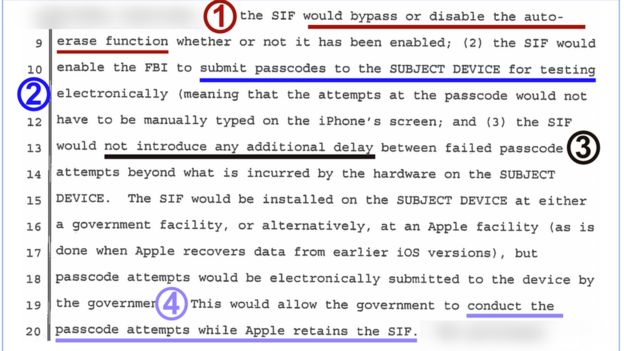 The FBI wants to be able to: Presumably only under a court order. |
W-K 666  Send message Joined: 18 May 99 Posts: 19048 Credit: 40,757,560 RAC: 67 
|
The public key is only used to generate the private key(s), and if you are really paranoid only for that session. |
 Lynn Lynn Send message Joined: 20 Nov 00 Posts: 14162 Credit: 79,603,650 RAC: 123 
|
This is just a game that Apple is playing to suck more profits out of simpletons willing to pay extra for the illusion of privacy. +1 |
Darth Beaver  Send message Joined: 20 Aug 99 Posts: 6728 Credit: 21,443,075 RAC: 3 
|
Go Apple !! fight for Capitalism and freedom . Fer gods sake unlock the dam phone they don't need to give them the software to do it , they can , Apple .. that is , it belongs to a terrorist for god sake . Take the stand they are for any other situation then I would support them but not on this . The person is dead and it's a criminal investigation ....where's common sense here !! 
|
 Lynn Lynn Send message Joined: 20 Nov 00 Posts: 14162 Credit: 79,603,650 RAC: 123 
|
Go Apple !! fight for Capitalism and freedom . +1 Please think about the victim's families. |
|
JLDun Send message Joined: 21 Apr 06 Posts: 573 Credit: 196,101 RAC: 0 
|
The FBI wants to be able to: I think it's the combination of these two considered the biggest risk. If you are able to bypass the "wipe after 10", it then effectively disappears out of the settings. And point 2 allows for quicker brute-force of any pin/password; if you have 'unlimited attempts' it basically says " my stuff is only protected for XX hours after someone starts trying."  
|
|
JLDun Send message Joined: 21 Apr 06 Posts: 573 Credit: 196,101 RAC: 0 
|
DOJ Lays Out Its Legal Case For Why Apple Should Help Crack An iPhone In the new motion, U.S. attorneys argue that Apple "retains the technical ability to comply" with the judge's order and that its "current refusal to comply with the Court's Order, despite the technical feasibility of doing so, instead appears to be based on its concern for its business model and public brand marketing strategy.  
|
 Gary Charpentier Gary Charpentier  Send message Joined: 25 Dec 00 Posts: 30640 Credit: 53,134,872 RAC: 32 
|
Latest is Apple says the pass code changed while the phone was in an evidence locker. http://abcnews.go.com/US/san-bernardino-shooters-apple-id-passcode-changed-government/story?id=37066070 Real smart move. Now they don't have a backup copy. A backup that would not be subject to the auto-wipe! A backup that by now all 10,000 possible codes could have been tried. So the case boils down to the Famous But Incompetent having to have someone else rescue their incompetent butts from their own stupidity. 
|
 janneseti janneseti Send message Joined: 14 Oct 09 Posts: 14106 Credit: 655,366 RAC: 0 
|
Latest is Apple says the pass code changed while the phone was in an evidence locker. I guess No Such Agency has a saying as well:) |

©2024 University of California
SETI@home and Astropulse are funded by grants from the National Science Foundation, NASA, and donations from SETI@home volunteers. AstroPulse is funded in part by the NSF through grant AST-0307956.